Our client, the head of the security service in the company in the financial sector, shared a real case about how they found the insider in the organization using Kickidler employee monitoring software and other technical means of information security.
At the request of the client we've changed some names in the story, including the name of the respondent, however the series of events hasn't been changed.
Kickidler: Tell us how you found out that there was an insider in your team.
Michael: Signals from management of client sales started appearing. Approximately since September the percent of extension of the use of our products had sharply declined. Of course, we started calling the clients, tried figuring out who made them a “better offer”. But the strange thing was, the beneficiary in almost all cases was different. Which meant that the version with the “enemy spy” inside the company didn't check out.
Kickidler: How did you make the decision that it was an insider then? Decline in sales can be caused by a number of factors.
Michael: One of the clients told us that he got calls from several organizations at once, which made us think of another idea. Together with marketing department we conducted a process of monitoring various Internet resources to find offers regarding the sale of client bases in our field of business. Several sources were found; we made a test purchase in the so-called “DarkNet” of the base that appeared identical to ours.
Kickidler: Were you already using Kickidler by then?
Michael: No, we weren't. We had (and still have) an installed DLP software that controls all operations with files. Access to corporate data is possible only from desktops – even for top management. If someone downloaded, sent by mail, loaded to the cloud, sent in the messenger or even printed and then scanned the client base, then with the probability of 99% we would catch that “leak” – provided, of course, the malefactor wasn't a “cool hacker”. After the above-mentioned incident we decided to download EMS (note: employee monitoring softwre) in addition to DLP, so that this tool could log all actions of the users at their personal computers.
Kickidler: Did you choose our program right away?
Michael: Well, in general, yes. It met our main requirements. We needed to have the screens of everybody who had access to CRM broadcasted, and, like I've said before, we needed to record all actions of the users at the computers. You fulfill these requirements better than similar softwares.
Kickidler: So how did the employee monitoring software help you find the malefactor?
Michael: We kept checking the resource where the client base was bought the last time. Until one day the information about updating appeared there. We made one more test purchase, and it turned out that the update was literally a day old. Which meant that approximately within two working days one more theft was committed. We started monitoring with the help of Kickidler actions of those who logged into CRM and analyzing employees' activity on the website. In your software (Kickidler) it is possible to use the filter and see all history of user's interactions with the chosen website or program. That's what helped us in the end.
Kickidler: And how did the malefactor steal the client base if it weren't recorded in operations with files? Did it take a lot of effort to find him?
Michael: We immediately understood that the base wasn't unloaded directly from CRM, because we bought it from that resource in the other format that was different from the formats, in which you can get it in CRM. There was one option left – someone photographed the pages of the base directly from the screen of the personal computer using a photographing device and then manually or through the service of optical character recognition translated them into text format.
Such search is hard work, but we considerably simplified it with one trick. We have around 150 people who have access to the base. From that number, 30 people have full access. Either one of these people could leak the base or it could be someone who gained access to the personal computer of the employee with full access.
Anyway, the trick was that usually the employee uses the list of tasks in CRM, plus he logs into client cards. To implement his plan, the malefactor needed to visit at least 10 pages in order to photograph them. Based on this observation, we created in Kickidler a violation of the web address, namely, of the 10th page of CRM base, and saw all the people who visited it.
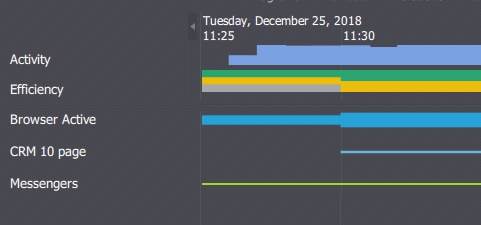
Then we looked at the videos of users' actions that were recorded by the video recording feature (Kickidler) on this page, identified suspicious activity of several employees, recorded time when this suspicious behavior occurred and looked through the CCTV footage during these time periods. And that's where we got lucky. Turned out that one of the managers during a lunch break photographed the screen of the personal computer on his phone when nobody was at the office. In fact, many suspected that employee anyway.
Kickidler: What's his future like?
Michael: I can't disclose such information, but I will tell this – he doesn't work for us anymore. Of course, the damage that he caused can't be undone, but at least we got rid of the saboteur who could do a lot of other evil things in the future.
Did you enjoy the article? Subscribe to us on social media.
Did you like this post? Follow us on social media.

 ENG
ENG 
