

Ensure your sensitive company data is protected with the help of our most extensive best Data Loss Prevention software
Kickidler Data Loss Prevention (DLP) enables businesses of all sizes to discover and classify sensitive data across their network, cloud, email, web as well as monitor and protect sensitive information from exposure by employees and third parties.

5000+ organizations from
60 countries rely on us
Protect all types of sensitive company data without interfering with work processes
regardless of the
size
of your business or the industry you operate in
Protect sensitive company data from loss due to accidental, negligent or fraudulent employee behavior with Kickidler DLP’s insider threat prevention features based on data-driven analytics, automated incident response and contextual user activity monitoring.
Kickidler Data Loss Prevention software is capable of detecting all types of insider threats and preventing them before they even happen or repelling them in the moment with real-time threat prevention tools.
Strengthen data security for the entire workforce across your company. As a highly effective data loss prevention solution, Kickidler provides businesses with features that aim to protect internal company data from any type of loss, including intentional insider attacks, malicious threats or simply accidental breaches caused by human error.
Keep your business protected in today’s complex digital landscape with user and entity behavior analytics. Malicious cyberattacks are becoming more sophisticated, and therefore threat detection methods need to be advancing as well in order to keep companies safe from attack.
Kickidler DLP solution relies on its extensive analytical reports and a sophisticated algorithm to identify and detect anomalous behaviors of endpoint users, which can be indicative of a potential attack.
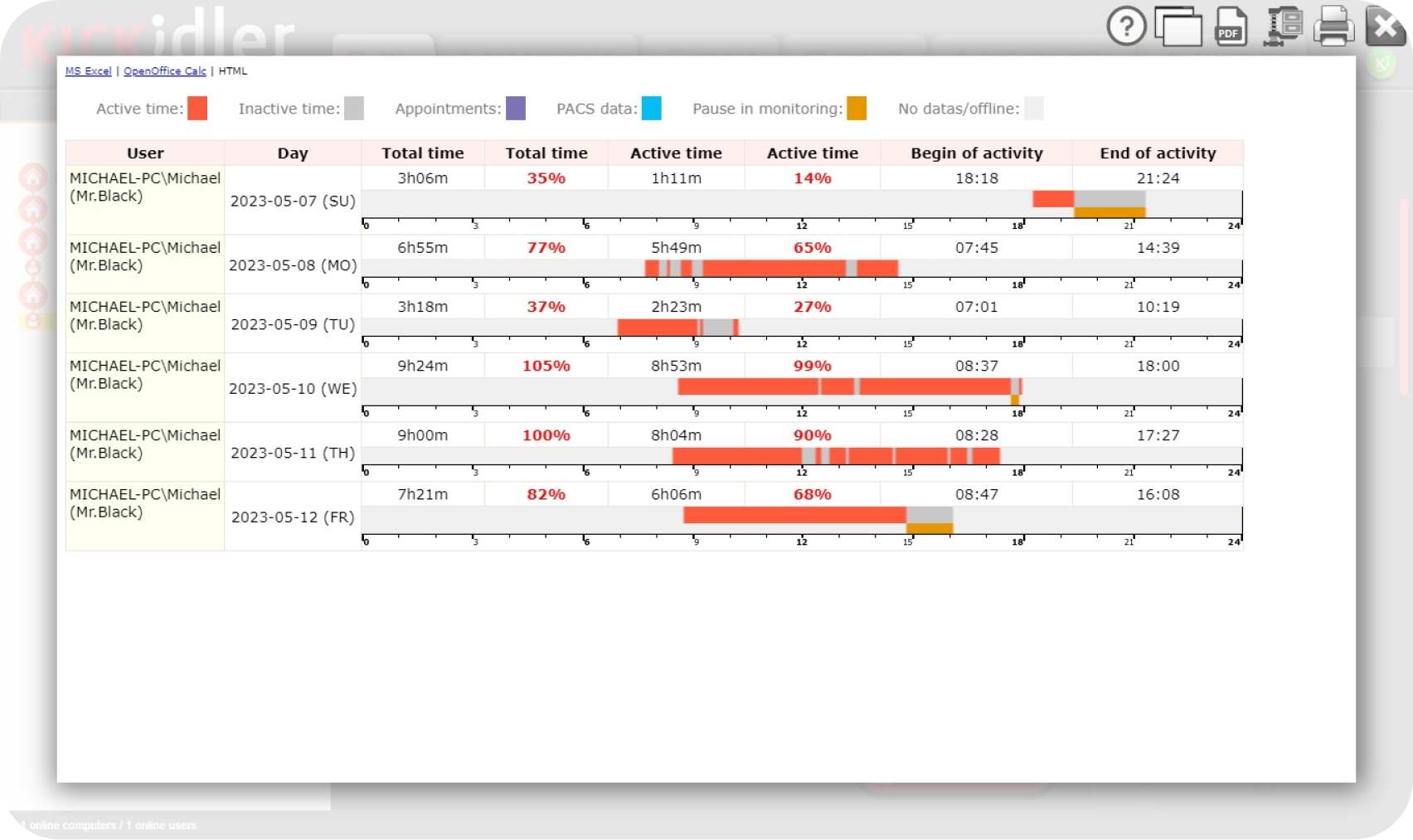
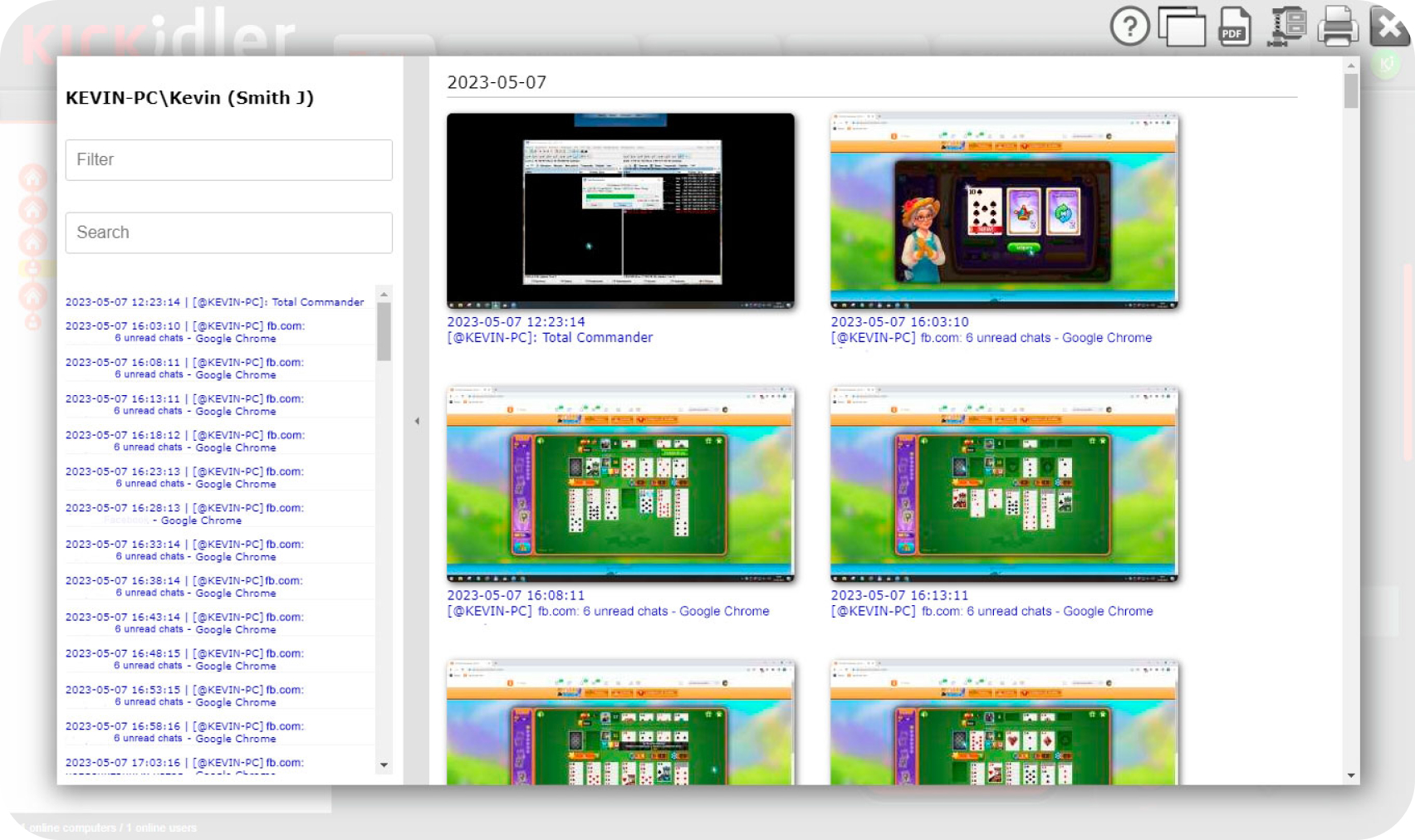
Keep track of your employees’ work activities with extensive endpoint monitoring. Block malicious or high-risk activities and get full reviews of employee activity. Kickidler supplies extensive data on engagement and productivity of all employees, whether they are remote, hybrid or in-office workers. With the help of this data loss prevention software, workforce trends can be easily identified to ensure managers make justified and unbiased decisions.
Go beyond basic employee monitoring with behavior analytics that provide data-backed insights into employee productivity, data security and compliance while at the same time maintaining employee privacy. Kickidler’s employee monitoring features enable managers to enhance business operations, track employee productivity and optimize their performance.
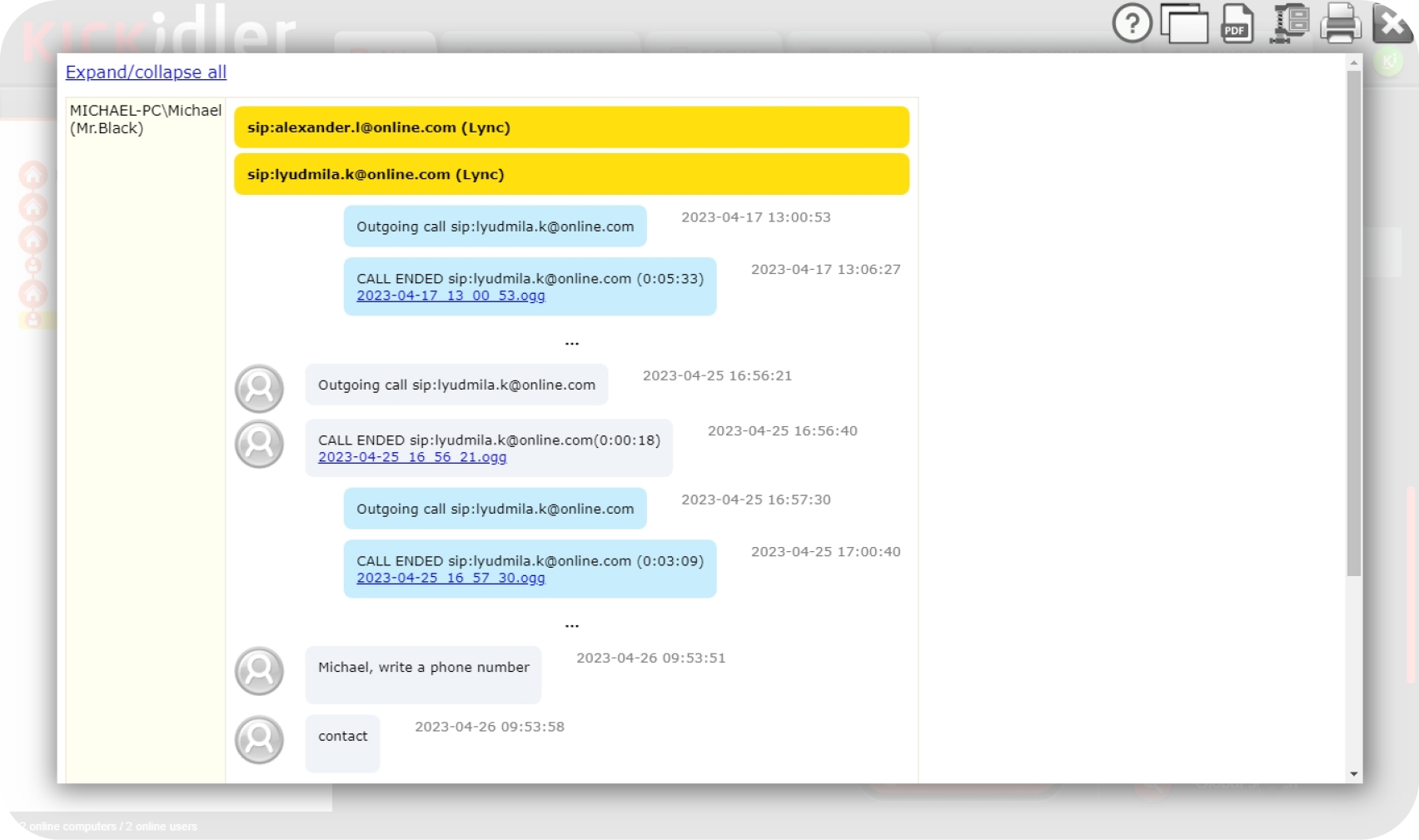
Still wondering if Kickidler is the right choice for you? Here are the main strengths
of our data loss
prevention tools that make us stand out from the competition

Secure company data against both malicious and unintentional threats from inside the organization
All user behavior deviations are being tracked and recorded, generating a consolidated report with statistics on resources used, categories of activity, and deviations from the corresponding standards
Notifications on violations and other critical user events appear in the notification area or browser window with a sound signal. There’s also the option of receiving notifications via SMS and email.
The software can intercept printed files in the spooler, thus enabling efficient tracking of every document printed by the employees.
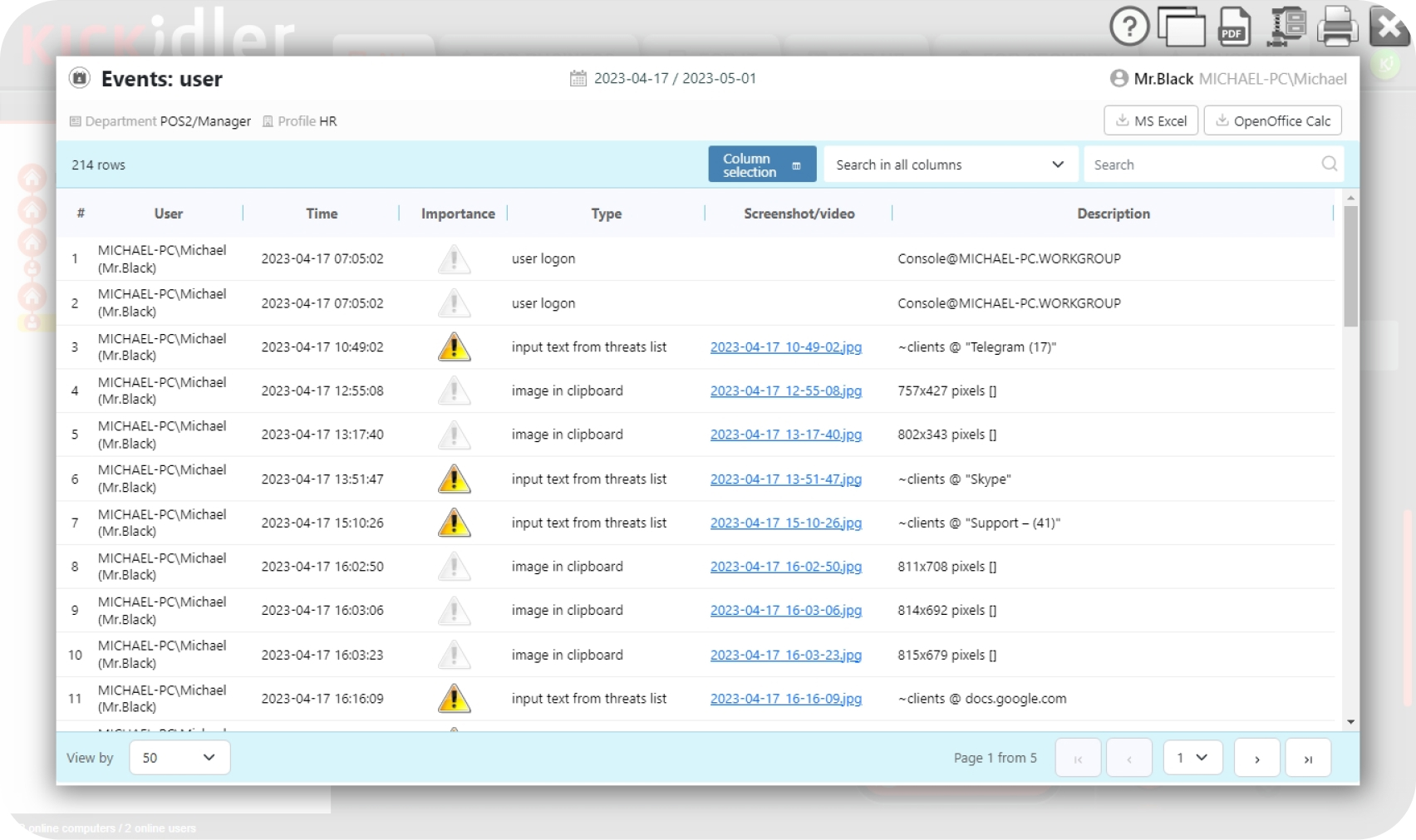
Search by tags, window titles, words recorded by the keylogger, applications and websites within the entire employee database, with the option to easily access screenshots of the identified time interval for each employee.
Managers can use the option of reviewing all the text, files and pictures on the employee’s clipboard.
The option of intercepting file duplication, deletion, and transferring is provided. It is also possible to create shadow copies when copying files to a flash drive. WebDav support is provided.
Administrators can restrict file transfers via file-sharing sites, email, online messengers, and social networks.
The software prevents employees from taking photos of their PC screens with their smartphones while running critical apps.

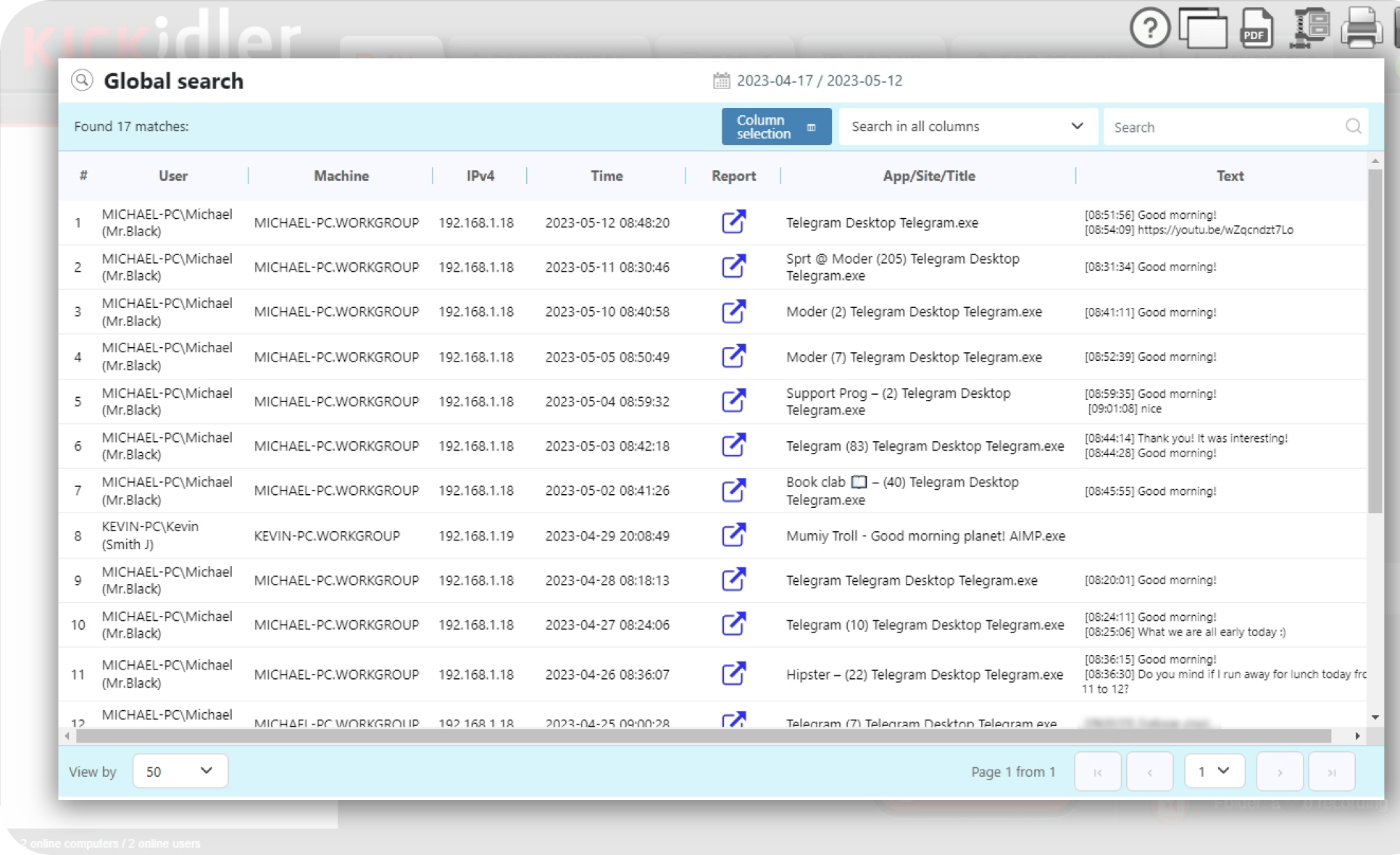
Protect company and customer data by detecting and preventing fraudulent activity
Hidden watermarks are placed on PrintScreen images so that they could be easily identified later if found in public domain.
The software allows recording any changes in critical documents.
If an employee behind their workstation is replaced by another person, the administrator gets alerted to this situation immediately. To recognize faces via webcams, an offline engine of our own design is used, based on a neural network. If another person (even another employee) is detected at the employee's workplace, their computer gets locked until said employee's username and password are entered once more.
The software enables interception and voice recording of conversations, with the option to transform captured audio into text and view it as a text file.
Administrator gets alerted when the software detects atypical user behavior, such as copying, sending or deleting certain files, copying text to the clipboard, opening particular browser tabs, etc.
The solution offers the option to restrict access to external flash drives or portable drives, block access to selected websites, as well as completely deny access to clipboards (or simply ban the PrintScreen key usage).
The solution displays changes in the hardware on the endpoint devices and all the installed/removed software.

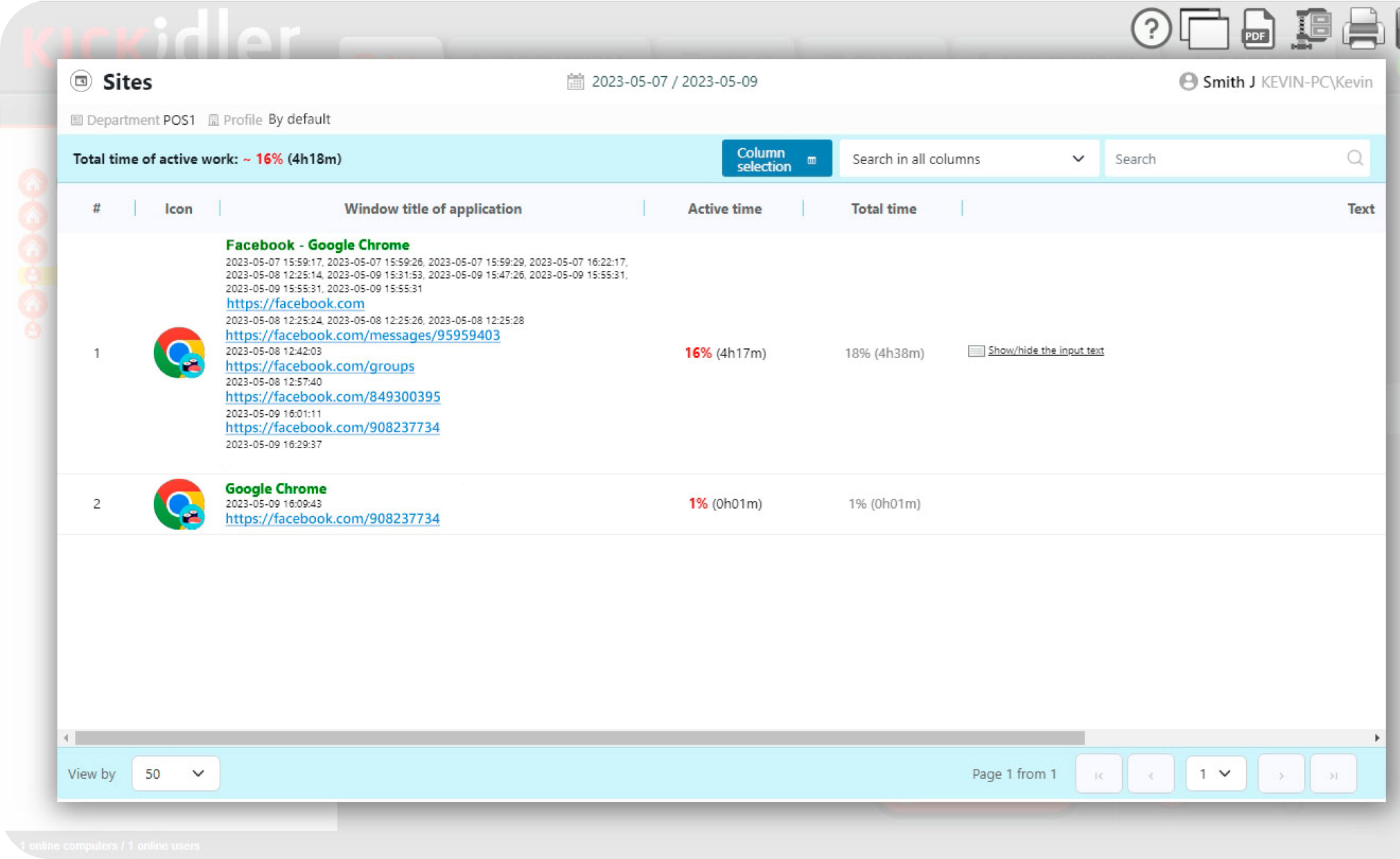
Analyze the work behavior of your employees with the help of our behavior-driven user activity monitoring functionality
Together with the keystroke logging feature, it ensures that all the input text – including in online messengers – is being monitored.
All GSM calls are being recorded. Real-time voice recognition of the employee offers the ability to save the conversation as a text file for further examination. It is also possible for the recording to turn on automatically once the employee starts talking.
The ability to view all search terms in different search engines is realized, along with the report on all the sites employees visited.
A report with a detailed overview of CPU and video card resource usage over time is generated.
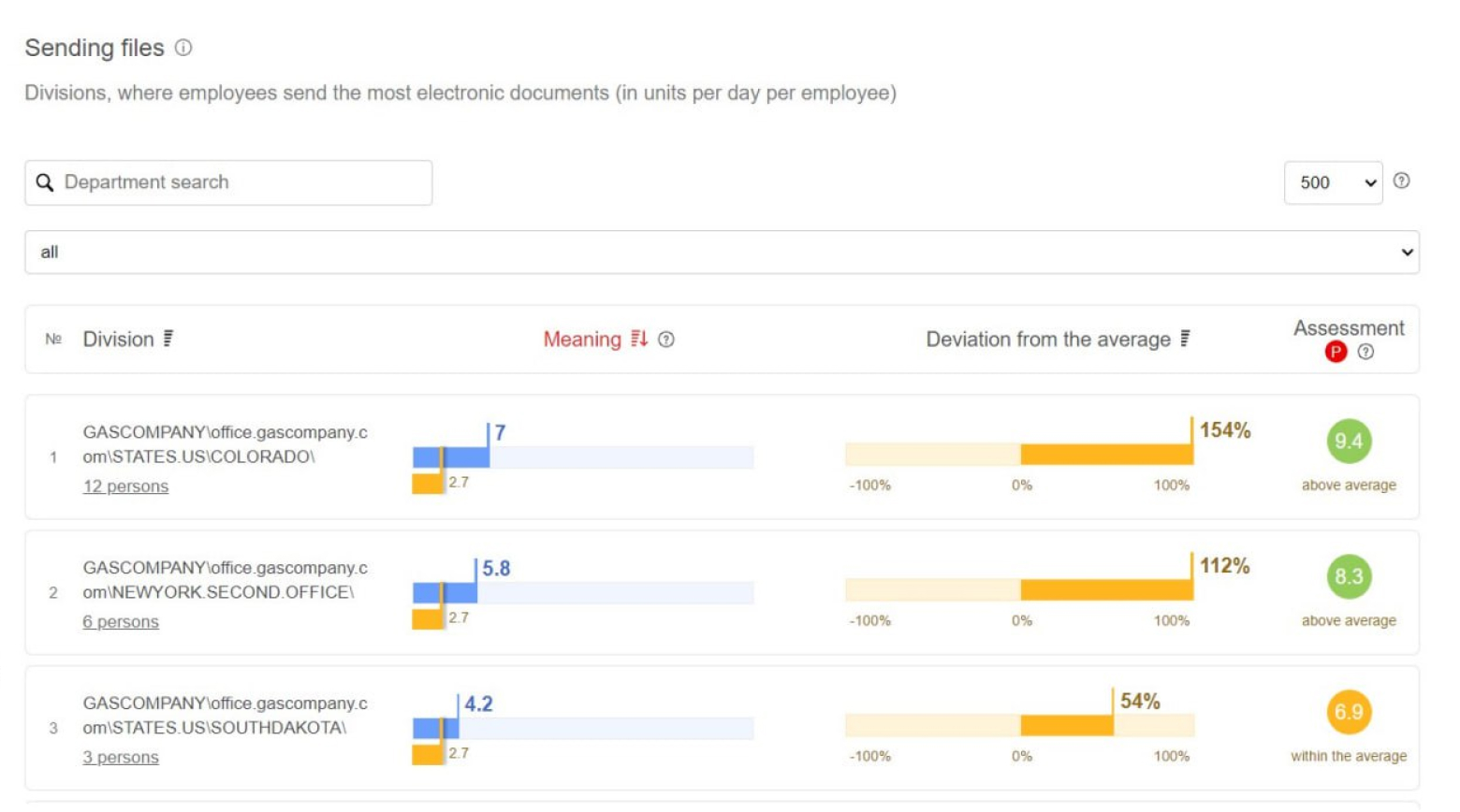
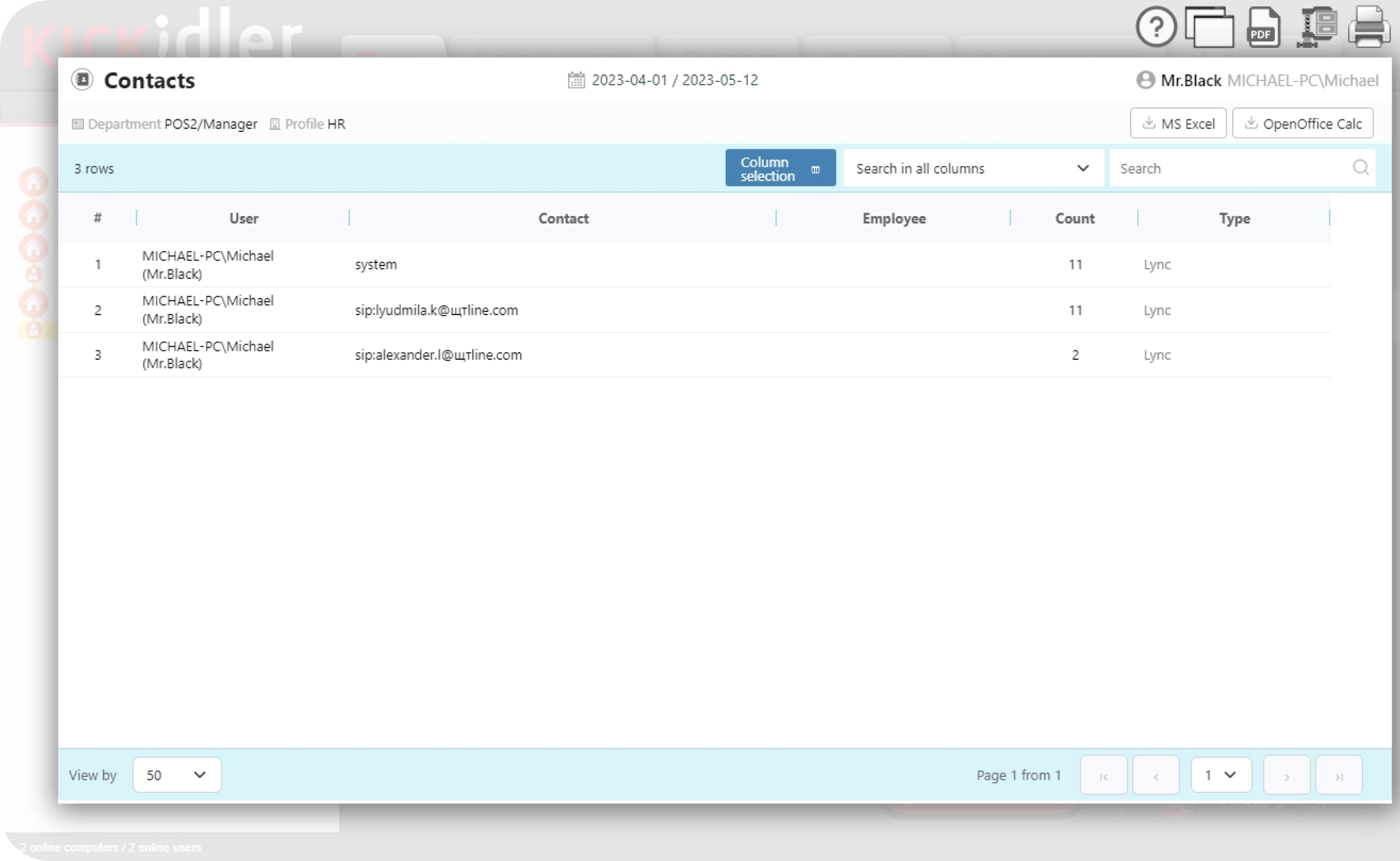
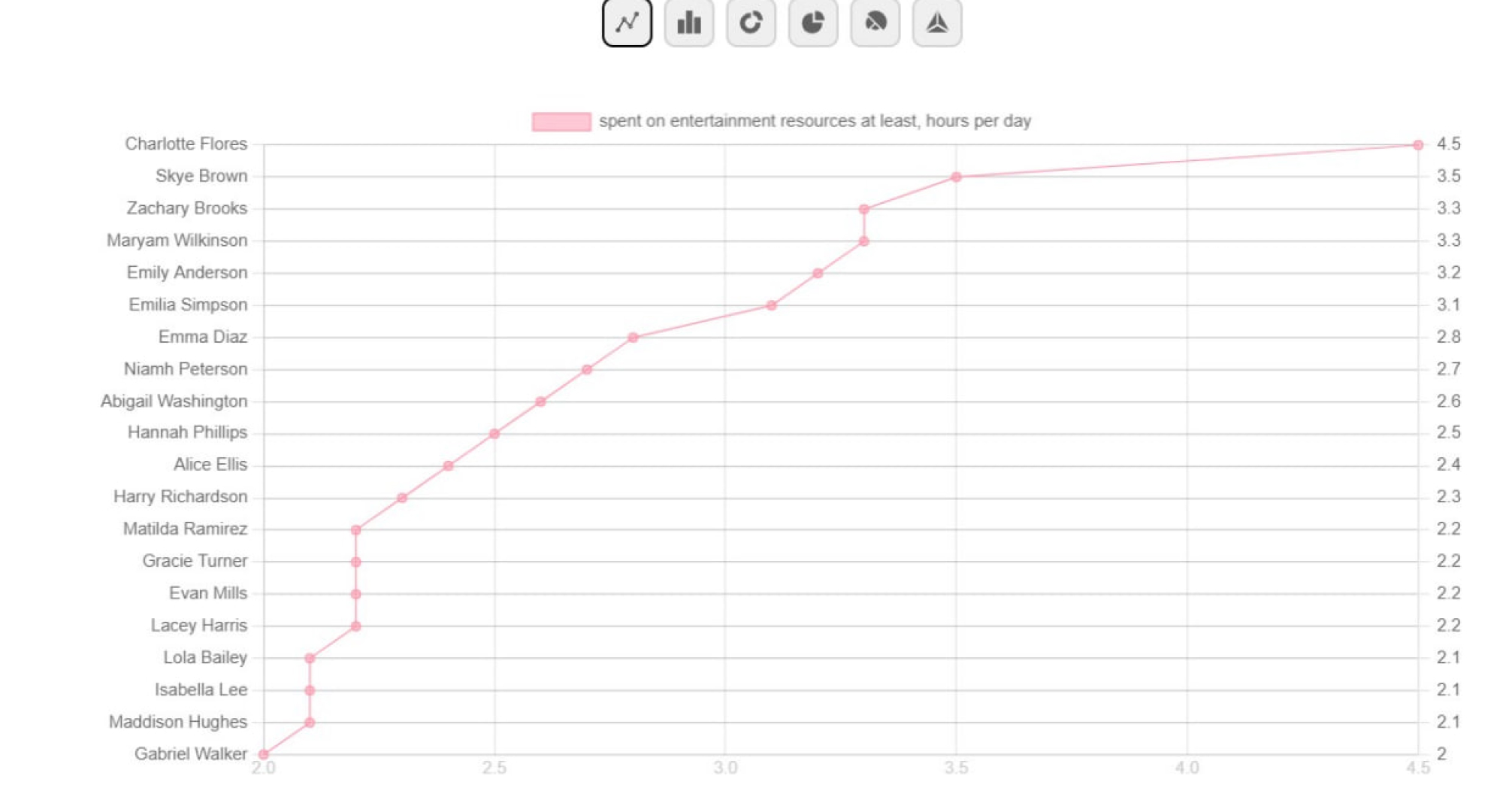
Managers can view a list of contacts with whom the user communicated via email, Skype, and instant messengers (along with its visual presentation in form of the convenient graph).
Ensure strong protection of your internal data by monitoring your employees’ mobile data usage
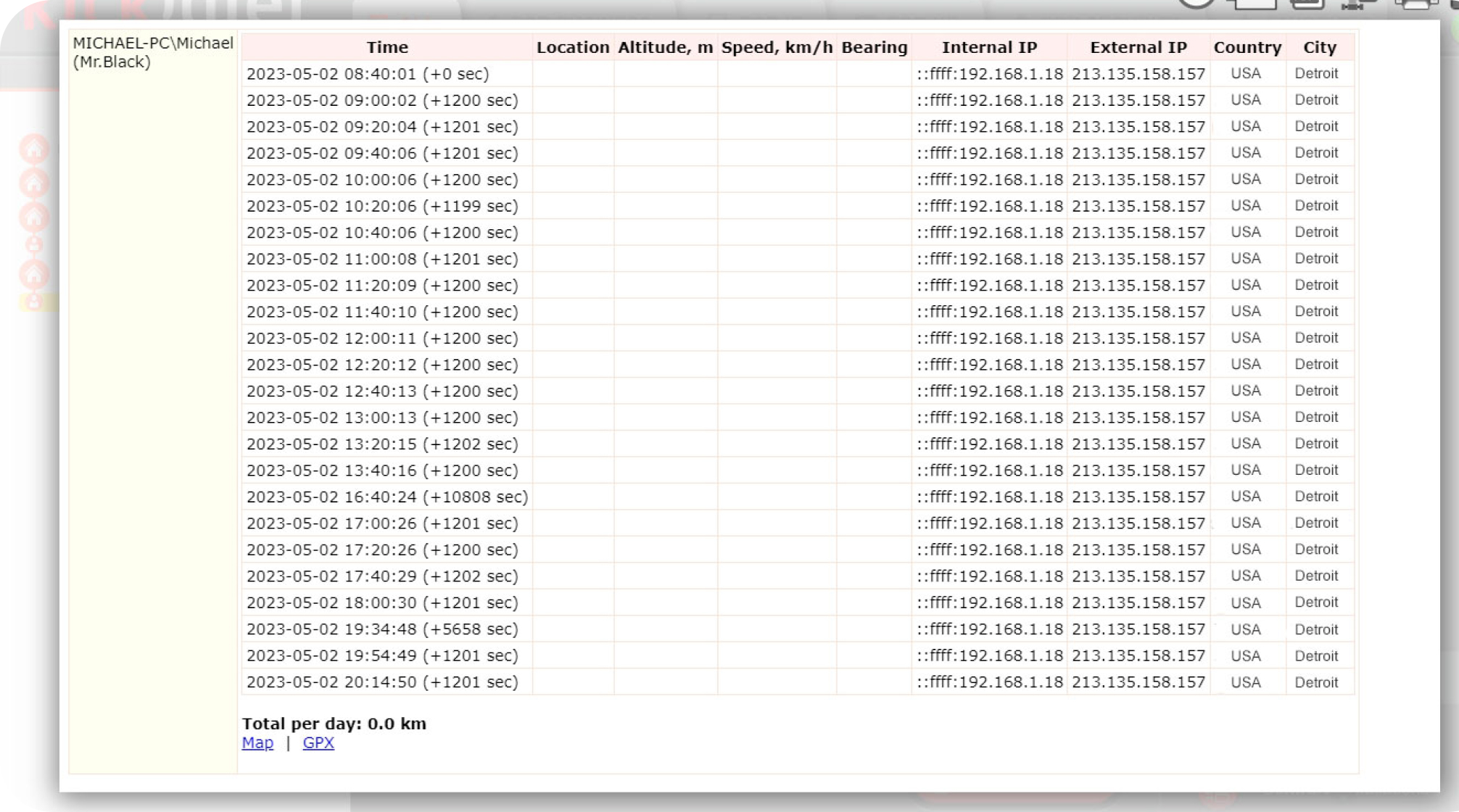
The software requests data from geolocation services to determine the employee’s location. Managers and security officers can find out the country and city of the employee's residence by external and internal IP addresses.
The software enables interception of text messages, e-mails, messengers and voice calls with their subsequent transmission to the server.
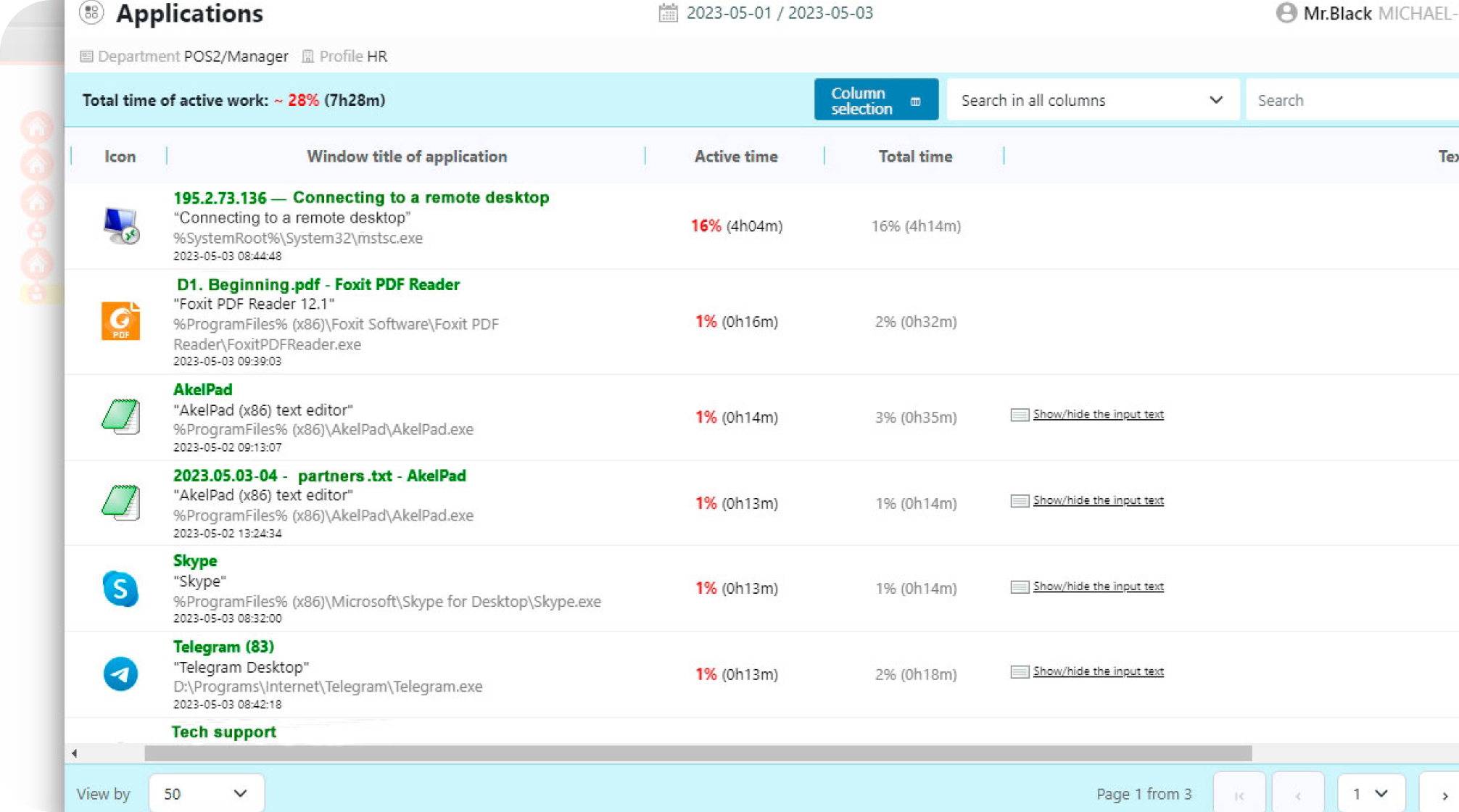
Running apps and visited websites are displayed, along with their full names and URLs, text inputs, and search terms.
Microphone activity gets recorded and can later be downloaded as an audio file for manager’s further convenience.
The keylogger feature provides the ability to monitor input text in all applications, including any instant messengers.
Monitor your employees during the working hours in order to increase
the
productivity of your team,
streamline internal work processes and maximize ROI
Managers can see actions of their employees as they’re happening, which helps them to get insights into employee productivity trends.
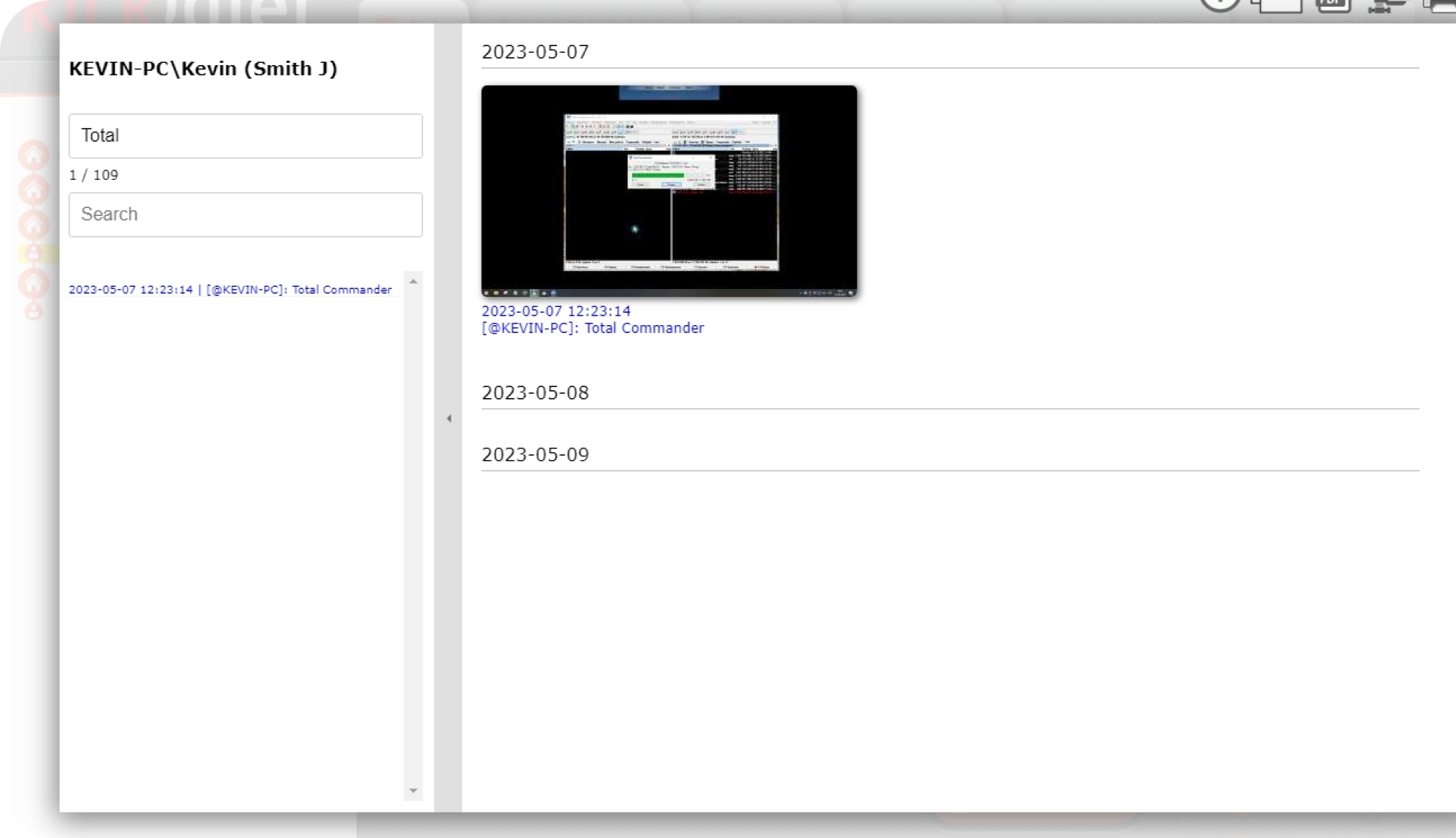
There is also an option to view employees’ actions after they’ve occurred, using video-quality recordings and screenshots that can help managers to review certain events or get irrefutable evidence of misconduct.
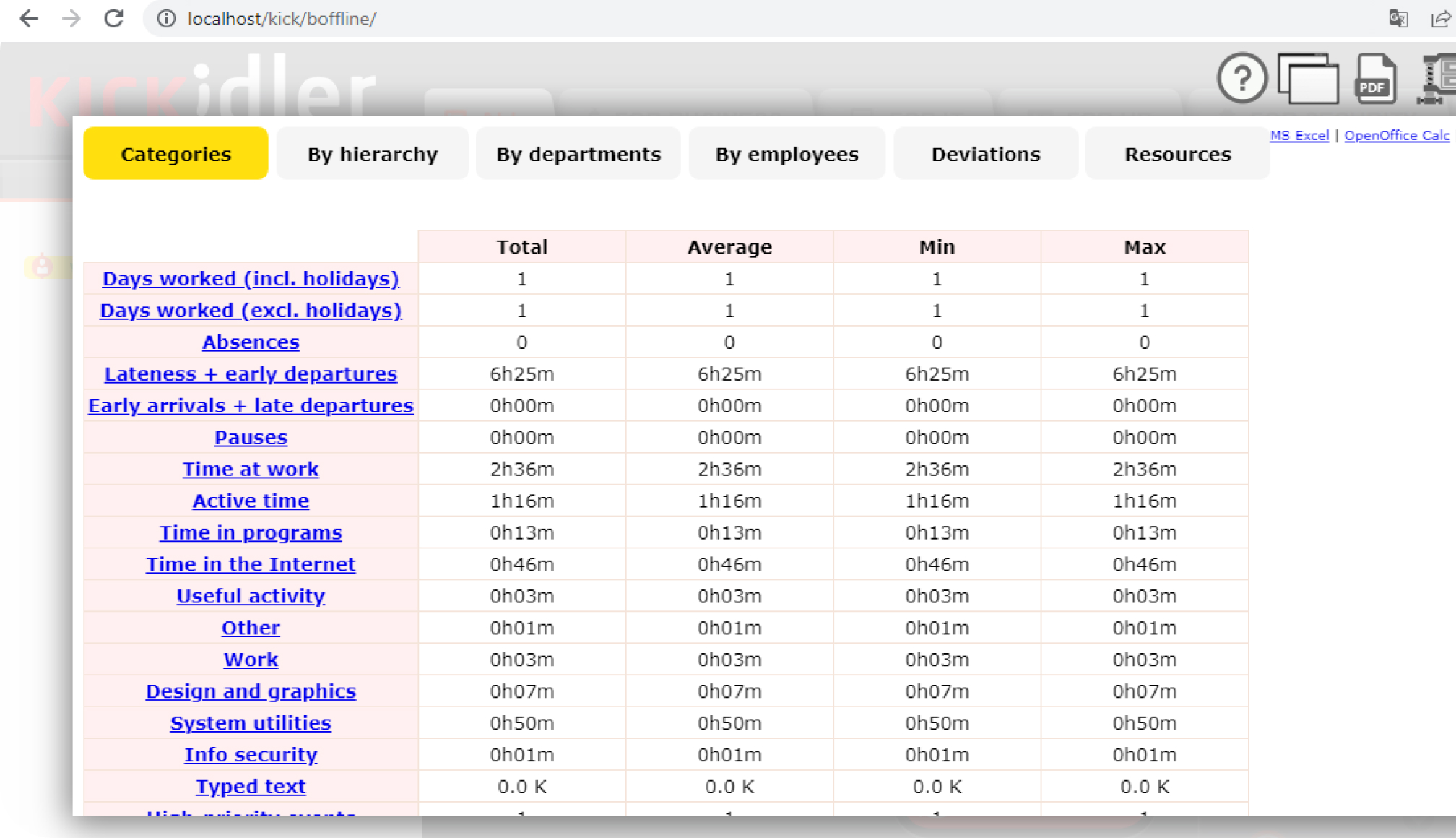
The software provides insights into employees’ daily activity, highlighting instances of absenteeism, times they’re late, as well as the amount of breaks they take during the working hours. It can also be synced with the Outlook calendar and other ACS integrations.
There is an option to capture individual screenshots from the employee's webcam or stream it as a single integrated video clip.
The software offers a customizable toolkit that categorizes employee activity into effective, ineffective or high-risk.
Managers are able to search specific information on individual users within generated reports (including fuzzy name matching).
Get key data on various work-related aspects of employee activity through Kickidler’s multi-level extensive reporting that simplifies complex data and analysis, presenting it as easy-to-understand visual charts and graphs.
With unique requirements of each business in mind, we offer the
cybersecurity
solution to address your
industry’s particular data protection needs
It is possible to assign different access rights to managers in terms of both viewing only certain reports and having access strictly to selected departments within the company's structure.
Our client-server channel is encrypted, with an additional option to configure https-access to the web-interface.
The software provides insights into employees’ daily activity, highlighting instances of absenteeism, times they’re late, as well as the amount of breaks they take during the working hours. It can also be synced with the Outlook calendar and other ACS integrations.
The software offers both public and stealth installation options, depending on the objectives you pursue.
Employees are able to switch the monitoring on and off themselves (this feature is especially useful when managing remote teams).
Employees won't be able to fake extensive involvement in work activities by having their keys stuck on the keyboard.
Managers have the option to promptly shut down or block all employees’ computers or run a script on the server via Telegram.

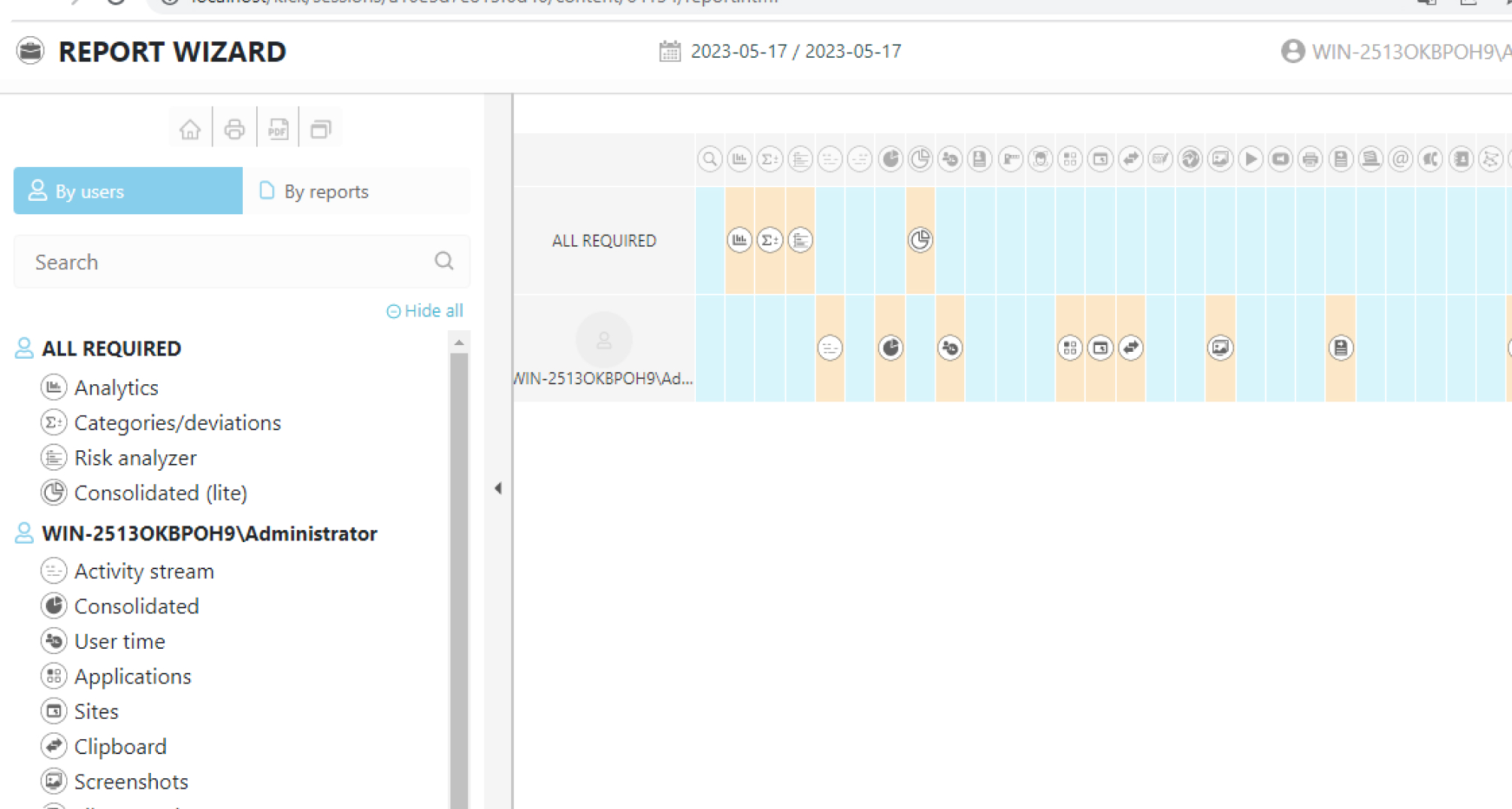
| Amount of users | Free Trial (up to 50 users) | Cost of a month license | Cost of 3 months license | Cost of 6 months license | Cost of annual license | Cost of a three-year license | Cost of perpetual license | Discount | Concierge support** |
| 1-99 users | 14 days | $20 | $50 | $80 | $132 | $264 | $320 | 0 | $10 |
| 100-499 users | 14 days | $14 | $35 | $56 | $92 | $184 | $224 | 30% | $7 |
| 500-4999 users | 30 days | $8 | $20 | $32 | $52 | $105 | $128 | 60% | $5 |
| 5000-20000 users | 30 days | $4 | $10 | $16 | $26 | $52 | $64 | 80% | $3 |
**DLP concierge support refers to a dedicated service that assists organizations in implementing and managing their Data Loss Prevention (DLP) strategies.
Here are the reasons why implementing our
Data Loss Prevention tool
is
essential for your business


Over 80% of companies that operate in the financial sector have 1,500+ sensitive files visible to all the employees
Implementing our Kickidler DLP tool prevents unscrupulous employees from data theft. The software scans and identifies the confidential information in organizations’ endpoints and allows users with administrator rights to encrypt or delete data at rest. Our solution addresses both internal and external threats, since it is imperative for organizations that collect and manage data to ensure information protection and to make sure that confidential data is protected.

More than 70% of consumers believe that businesses aren’t doing enough to secure their personal information
Companies that implement Kickidler Data Loss Prevention solution are able to achieve regulatory compliance with HIPAA, GDPR, and so on, avoiding fines and other damages imposed by regulatory entities. Kickidler’s extensive analytical features, automated incident responses and contextual user monitoring strengthen internal company cybersecurity.

Around 60% of employees have brought data from their previous place of work to their current employer
By implementing Kickidler DLP tool, executives can ensure their intellectual property, company financials, trade secrets, credit card data, and other pieces of sensitive data are protected. Insider threat prevention and data misconduct detection backed by data-driven endpoint monitoring helps businesses to safeguard sensitive and confidential internal data.

Approximately 30% of large businesses and 25% of small businesses have encountered insider threats and data leaks
Our solution helps companies to stop sensitive data leakage and data theft by applying appropriate cybersecurity protocols at the endpoint, from logging potential insider threats to real-time blocking. With Kickidler DLP solution, managers can identify users that fail to follow data security policies and pinpoint situations that can lead to a policy violation or data leakage.
Deploy our cross-platform Data Loss Prevention software that
works
on
Windows, Mac and Linux in a way that
suits your business needs

Kickidler data loss prevention tool offers continuous data loss prevention across Windows, Mac and Linux endpoints. Here are our flexible deployment options:
Maintain complete ownership of your data with Kickidler on-premise deployment. Our software is installed in just a few clicks, does not overload the CPU, and can be run even on slow endpoints.
It takes simply a few minutes to get you going with Kickidler cloud version. Our scalable and flexible solution doesn’t require any maintenance, is updated on a regular basis, and is completely trustworthy.
You can get worldwide access to our Kickidler data loss prevention tool with the help of a terminal server. The software is run on the server, and it allows for connection of a number of endpoints. Our solution can operate across multiple servers and one central database.
Our Kickidler DLP thin client version is used for browser-based employee monitoring. A virtualized desktop setup makes implementation of the software as smooth and hassle-free as possible.
For more details on the comparison of DLP software, read our blog on Top 8 Best DLP Software.
This calculation is approximate and should only be used as a reference.
The actual numbers will always
vary from the estimated ones.
Not certain if our top DLP tool is the right fit for you?
Explore
other
solutions in our product suite

Being a more laid-back monitoring version, Kickidler Time Tracking provides managers with tools that automate time tracking, analyze employee productivity, and help remote workers become more self-organized through the use of the self-monitoring interface (Autokick).
Kickidler TT automatically records the hours employees spend at their PCs, factoring in their work schedule and providing an accurate record of how much time employees spend on certain websites and in particular applications.
Its features include the report on working hours, automatically generated timesheet, overall time report, and the report on websites and applications.
Kickidler TT also determines just how productive employees are during the workday. The software utilizes one-second increments, making its reports extremely accurate. These reports include the efficiency report, the "Details of the Day" report, the dynamics report, and the overall rating of employees.
For autonomous employee self-monitoring, Kickidler offers Autokick, which is a set of tools that includes a self-monitoring interface, which allows employees to see their own productivity metrics, enable and disable the monitoring, as well as receive automatic notifications on any work schedule violations (for example, working for too long without any breaks).
Check Kickidler TTMonitoring version is a full-on, “Zero Trust” monitoring software that contains all the tools included in the Kickidler Time Tracking package along with several other tools that enable visual monitoring.
These features include real-time monitoring of an unlimited number of screens, screen video recording, violations monitoring, keystroke logging, and remote access to employees’ PCs.
Kickidler EM offers managers a truly in-depth look into the activities of their employees.
Check Kickidler EMOur experience in elevating internal business processes
of companies
speaks for itself. Learn about it firsthand
Data loss prevention is the process of protecting sensitive data from potential leaks by monitoring data usage and preventing it from being exfiltrated in an unauthorized manner.
Data loss prevention is a general term used to describe data protection measures against all types of threats, which include third-party cyber attacks and insider threats.
In cybersecurity, DLP stands for data loss prevention. It is defined as a set of measures to protect data from being shared or exfiltrated in an unauthorized manner.
Data Loss Prevention solutions protect sensitive categories of data directly by offering security policies that allow the control of data transfers.
DLP software typically performs both content inspection and contextual analysis of data in motion on the network, in use on a managed endpoint device, and at rest in storage areas or on desktops. Data loss prevention remote or offline variants are available among most DLP software.
Data loss prevention remote or offline variants are available among most DLP software
Using modern cybersecurity solutions like endpoint monitoring can improve businesses’ cybersecurity and strengthen their insider threat prevention protocols.
Typically, a DLP tool alerts system administrators of any anomalous behavior that might indicate an insider threat, enables monitoring of certain users, and provides automated responses, such as blocking high-risk activities.
Kickidler DLP solution is crucial for many businesses, seeing how it protects against both malicious and negligent insider threats, as well as helps to meet the compliance requirements of data protection regulations. Download Kickidler DLP.
The software helps companies to safeguard valuable business information and minimize the risk of a data breach, which can lead to economic losses, reputational risk, or legal problems.
Kickidler DLP is an advanced data loss prevention solution for businesses that are concerned with their data security. Companies of any size and in any industry who want to strengthen their data security protocols and protect sensitive internal data against insider threats can benefit from using Kickidler Data Loss Prevention software. Download Kickidler DLP.
Data loss prevention is the process of protecting sensitive data from potential leaks by monitoring data
usage and preventing it from being exfiltrated in an
unauthorized manner.
Data loss prevention is a general term used to describe data protection measures against all types of
threats, which include third-party cyber attacks and insider
threats.
We are here for you in case you have any questions about the product, need advice on its features or require additional help with its implementation. You can get data loss prevention free trial for 14 days.
You can also get acquainted with additional useful information: